- Shodan
 Shodan
, the official definition of himself Computer Search Engine (Computer
Resource Search Engine), is American man John Mase Li spent nearly 10
years to build a search engine that can search almost all US industrial
control and connected to the network system .Shodan Unlike traditional
search engines such as Google, use Web crawlers to traverse your entire
site, but directly into the channel behind the Internet, various types
of port equipment audits, and never stops looking for the Internet and
all associated servers, camera, printers, routers , and so on. Shodan
month will be at about 500 million server around the clock to gather
information.
Shodan
, the official definition of himself Computer Search Engine (Computer
Resource Search Engine), is American man John Mase Li spent nearly 10
years to build a search engine that can search almost all US industrial
control and connected to the network system .Shodan Unlike traditional
search engines such as Google, use Web crawlers to traverse your entire
site, but directly into the channel behind the Internet, various types
of port equipment audits, and never stops looking for the Internet and
all associated servers, camera, printers, routers , and so on. Shodan
month will be at about 500 million server around the clock to gather
information.
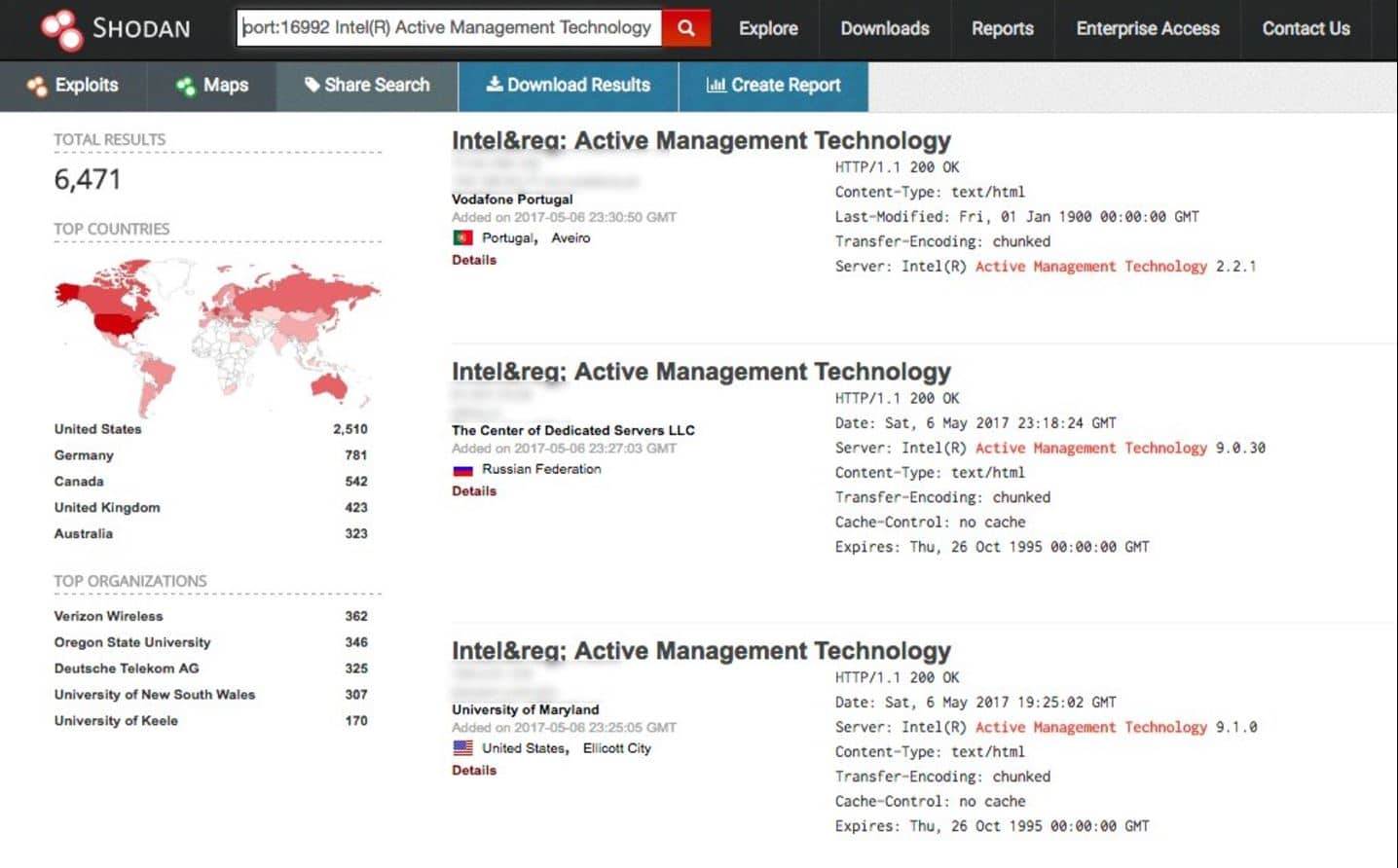
This engine can search, locate all devices connected to the network server. Shodan works produced by various types of port equipment system flag information (banners) audits generate search results, so when you use it, the need to understand a little knowledge of the system flag information.
Numerous industrial control computer, waterworks and power grid and other automation systems are connected to the network, some of which exist loopholes , moderate levels of hackers will be able to dive into these systems. Industrial control computer firewall protection usually at work, but the protection of a firewall can easily be connected to the network and erosion. Shodan tutorial, please visit here. - ZoomEye
 ZoomEye is a search engine for cyberspace that lets the user find specific network components(ip, services, etc.).ZoomEye API is a web service that provides convenient access to ZoomEye features, data, information over HTTPS. The platform API empowers developers to automate, extend and connected with ZoomEye. You can use the ZoomEye platform
API to programmatically create apps, provision some add-ons and perform
some automate tasks. Just imagine that what you could do amazing stuff
with ZoomEye.
ZoomEye is a search engine for cyberspace that lets the user find specific network components(ip, services, etc.).ZoomEye API is a web service that provides convenient access to ZoomEye features, data, information over HTTPS. The platform API empowers developers to automate, extend and connected with ZoomEye. You can use the ZoomEye platform
API to programmatically create apps, provision some add-ons and perform
some automate tasks. Just imagine that what you could do amazing stuff
with ZoomEye. - Censys
 Censys
is a search engine that allows computer scientists to ask questions
about the devices and networks that compose the Internet. Driven by
Internet-wide scanning, Censys lets researchers find specific hosts and
create aggregate reports on how devices, websites, and certificates are
configured and deployed. [more information]
Censys
is a search engine that allows computer scientists to ask questions
about the devices and networks that compose the Internet. Driven by
Internet-wide scanning, Censys lets researchers find specific hosts and
create aggregate reports on how devices, websites, and certificates are
configured and deployed. [more information]
Thursday, 29 June 2017
Top 3 Search Engine for Penetration Tester
Here I will introduce the three Web vulnerability search engine.









0 comments:
Post a Comment